Check Point Software Technologies Ltd., the largest pure-play security vendor globally, provides industry-leading solutions, and protects customers from cyberattacks with an unmatched catch rate of malware and other types of attacks. Check Point offers a complete security architecture defending enterprises’ networks to mobile devices, in addition to the most comprehensive and intuitive security management. Check Point first pioneered the industry with FireWall-1 and its patented stateful inspection technology.
As Sirius Information Technologies we are working with Check Point to secure our customers’ IT Infrastructure. Check Point provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platform, reducing complexity and lowering the total cost of ownership. Whether you need next-generation security for your data center, enterprise, small business or home office, Check Point has a solution for you!
With Check Point Security products you can secure your network from external and internal threats. Check Point’s blade architecture protects your organization against the most sophisticated and dangerous GEN-V cyber-attacks.

Our security team can provide you with a FREE onsite security assessment service with Check Point products that gives you a complete threat & risk analysis of your IT infrastructure that shows:
-
Access to high risk web applications
-
Malware infected computers
-
Exploited vulnerabilities and attacks
-
Data leakage incidents
-
Recommendations to protect you network

Check Point provides three packages for comprehensive network security
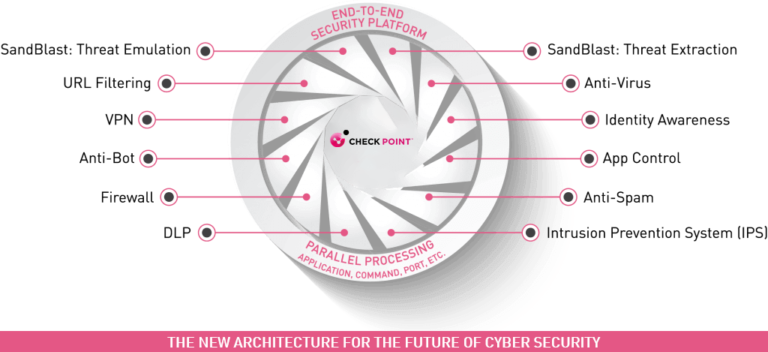
Next Generation Threat Extraction (NGTX) - GEN V Security
Includes multi-layered protection from known threats AND zero-day attacks using SandBlast Threat Emulation, SandBlast Threat Extraction, Antivirus, Anti-bot, IPS, App Control, URL Filtering and Identity Awareness.
Next Generation Threat Prevention (NGTP) - Gen IV Security
Includes multi-layered protection from known, signature-based threats including Antivirus, Anti-Bot, IPS, App Control, URL Filtering and Identity Awareness.
Next Generation Firewall (NGFW) - GEN III Security
Includes multi-layered protection from known, signature-based threats including Firewall, VPN, IPS, Application Control, Identity Awereness & Content Awereness
Software / Security Blades
Software Blade is a security function or module which allows you to manage your IT Security based on your needs. Software Blades are cost efficient. Blades can be enabled easily and managed centrally from Check Point’s Smart Dashboard.
 The Check Point Firewall Software Blade builds on the award-winning technology first offered in Check Point’s FireWall-1 solution to provide the industry’s strongest level of gateway security and identity awareness. Check Point’s firewalls are trusted by 100% of the Fortune 100 and deployed by over 170,000 customers, and have demonstrated industry leadership and continued innovation since the introduction of FireWall-1 in 1994.
The Check Point Firewall Software Blade builds on the award-winning technology first offered in Check Point’s FireWall-1 solution to provide the industry’s strongest level of gateway security and identity awareness. Check Point’s firewalls are trusted by 100% of the Fortune 100 and deployed by over 170,000 customers, and have demonstrated industry leadership and continued innovation since the introduction of FireWall-1 in 1994.
![]() The Check Point Intrusion Prevention System (IPS) Software Blade combines industry-leading IPS protection with breakthrough performance at a lower cost than traditional, stand-alone IPS solutions. The IPS Software Blade delivers complete and proactive intrusion prevention—all with the deployment and management advantages of a unified and extensible next-generation firewall solution.
The Check Point Intrusion Prevention System (IPS) Software Blade combines industry-leading IPS protection with breakthrough performance at a lower cost than traditional, stand-alone IPS solutions. The IPS Software Blade delivers complete and proactive intrusion prevention—all with the deployment and management advantages of a unified and extensible next-generation firewall solution.
![]() The Check Point Application Control Software Blade provides the industry’s strongest application security and identity control to organizations of all sizes. It enables IT teams to easily create granular policies—based on users or groups—to identify, block or limit usage of over 250,000 Web 2.0 applications and widgets.
The Check Point Application Control Software Blade provides the industry’s strongest application security and identity control to organizations of all sizes. It enables IT teams to easily create granular policies—based on users or groups—to identify, block or limit usage of over 250,000 Web 2.0 applications and widgets.
The Check Point URL Filtering Software Blade integrates with Application Control, allowing unified enforcement and management of all aspects of Web security. URL Filtering provides optimized Web security through full integration in the gateway to prevent bypass through external proxies; integration of policy enforcement with Application Control for full Web and Web 2.0 protection; and UserCheck empowers and educates users on Web usage policy in real time.
![]() The Check Point Identity Awareness Software Blade provides granular visibility of users, groups and machines, providing unmatched application and access control through the creation of accurate, identity-based policies. Centralized management and monitoring allows for policies to be managed from a single, unified console.
The Check Point Identity Awareness Software Blade provides granular visibility of users, groups and machines, providing unmatched application and access control through the creation of accurate, identity-based policies. Centralized management and monitoring allows for policies to be managed from a single, unified console.
![]() The Check Point IPsec VPN Software Blade provides secure connectivity to corporate networks for remote and mobile users, branch offices and business partners. The Software Blade integrates access control, authentication and encryption to guarantee the security of network connections over the public Internet.
The Check Point IPsec VPN Software Blade provides secure connectivity to corporate networks for remote and mobile users, branch offices and business partners. The Software Blade integrates access control, authentication and encryption to guarantee the security of network connections over the public Internet.
![]() The Check Point Anti-Spam and Email Security Software Blade provides comprehensive protection for an organization’s messaging infrastructure. A multidimensional approach protects the email infrastructure, provides highly accurate spam protection, and defends organizations from a wide variety of virus and malware threats delivered within email. Continual updates assure that all threats are intercepted before they spread.
The Check Point Anti-Spam and Email Security Software Blade provides comprehensive protection for an organization’s messaging infrastructure. A multidimensional approach protects the email infrastructure, provides highly accurate spam protection, and defends organizations from a wide variety of virus and malware threats delivered within email. Continual updates assure that all threats are intercepted before they spread.
![]() The Check Point DLP Software Blade combines technology and processes to revolutionize Data Loss Prevention (DLP), helping businesses to pre-emptively protect sensitive information from unintentional loss, educating users on proper data handling policies and empowering them to remediate incidents in real-time.
The Check Point DLP Software Blade combines technology and processes to revolutionize Data Loss Prevention (DLP), helping businesses to pre-emptively protect sensitive information from unintentional loss, educating users on proper data handling policies and empowering them to remediate incidents in real-time.
The Check Point Threat Emulation prevents attacks from zero-day and undiscovered threats. The technology protects against vulnerabilities and malware variants in email attachments and file downloads by discovering malicious activity using advanced behavioral analysis of threats in virtual environments.
The Check Point Anti-Bot Software Blade detects bot-infected machines, prevents bot damages by blocking bot C&C communications, and is continually updated from ThreatCloud™, the first collaborative network to fight cybercrime.
The enhanced Check Point Antivirus Software Blade stops incoming malicious files. Using real-time virus signatures and anomaly-based protections from ThreatCloud™, the first collaborative network to fight cybercrime, the Antivirus Software Blade detects and blocks malware at the gateway before the user is affected.
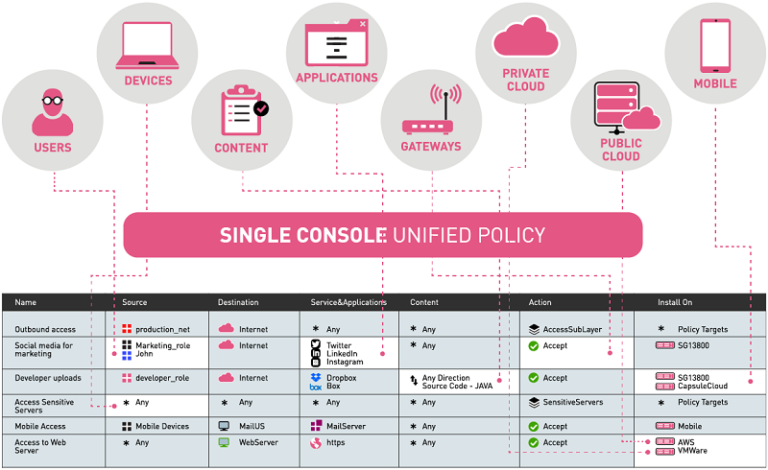
Unified Security Management