

Gartner® Report: How to Prepare for Ransomware Attacks
Check Point Harmony
The Industry’s first unified security solution for users, devices and access
Protecting today’s hyper-distributed workspace requires endless security functions across user devices, applications, and networks. However, stitching together point solutions often leaves security gaps and creates a cumbersome infrastructure that is difficult to manage and scale. Harmony offers an alternative that saves you the overhead and increases security.
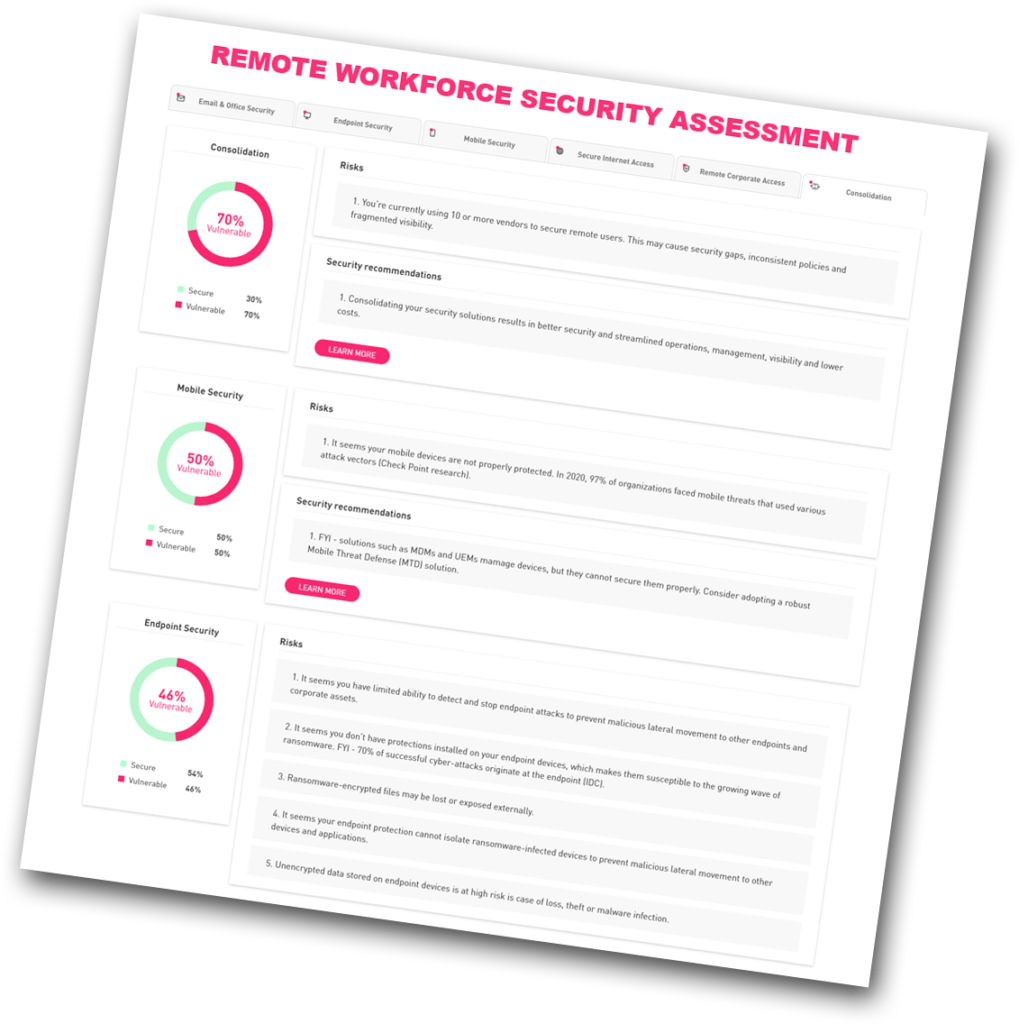
Find Your Security Gaps in 5 Minutes
Take our online remote workforce security assessment to understand your organization’s security gaps and how to close them, including insights into your:
- Endpoints’ resilience to ransomware
- Internet access risk exposure
- Remote access strategy strength
- Office 365 and G Suite protection level
- Vulnerability to mobile-related attacks
Find Your Security Gaps in 5 Minutes
With 57% of 1200 security professionals reporting that more than half of their workforce works remotely at least two days a week, the question of how these organizations secure their hybrid workforce arises.
In our 2022 Workforce Security Report, we share the full insights into the state of workforce security.

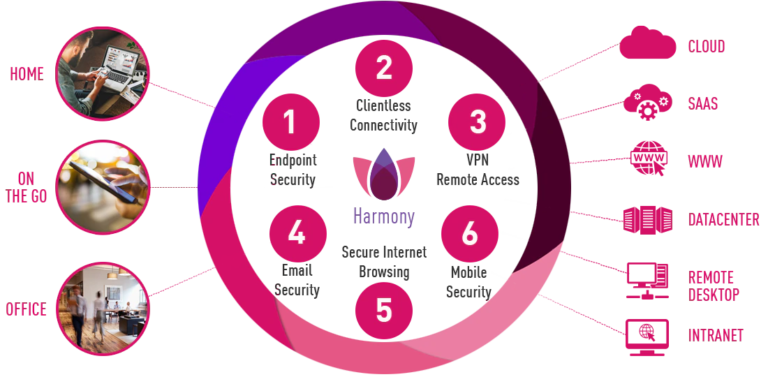
Harmony Unifies 6 Cloud-based Security Products to Keep Remote Workforce 100% Safe
Wherever you connect from, whatever you connect to, and however you connect – Your home, your devices, your privacy and your organizational data are secured and protected from any cyber threat.
Watch The Session: Writing The Next Chapter In Remote Workforce Security
Two years into the pandemic, the world is still predominantly working remotely. With users working anywhere and using their mobile phones and laptops to access corporate applications, your attack surface has never been wider.
Check Point Harmony delivers the highest level of security for remote users in a single solution that is easy to use, manage and buy. In this session, we present the new capabilities of the Harmony suite products and how they help you better secure your remote workforce.
Harmony: 360° User Protection Against All Attack Vectors
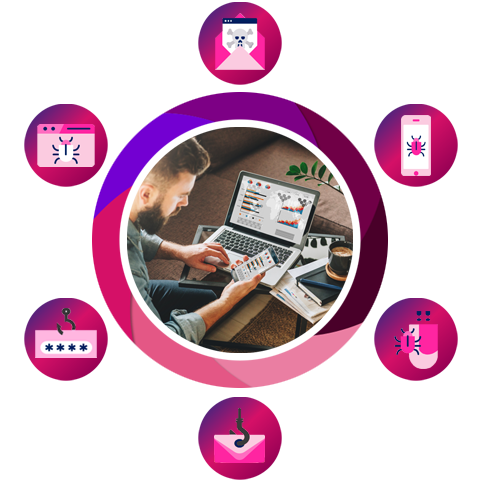
Whether it’s a phishing attempt, a malicious email attachment, or zero-day ransomware, Harmony protects users from all cyber threats, across all attack vectors. Powered by revolutionary AI engines and the industry’s most extensive threat intelligence network, Harmony stop attacks before they happen.
The Harmony Product Suite
Endpoint Security
A complete endpoint security solution built to protect user PCs and laptops from today’s complex threat landscape.
- Full Endpoint Protection from the most imminent threats such as ransomware, phishing, and malware
- Fastest recovery to enable quickly minimize breach impact with autonomous detection and response


Secure Internet Browsing
Enable a secure, fast, and private internet browsing experience with the industry’s first in-browser protection to inspect 100% of SSL traffic.
- Prevent malware downloads
- Prevent phishing attacks and corporate credential reuse
- Block access to websites deemed inappropriate by company policies
Email Security
Complete protection for Office 365 and G Suite.
- Block sophisticated phishing attacks
- Block malware without impacting productivity
- Protect sensitive business data (DLP)
- Prevent account takeover


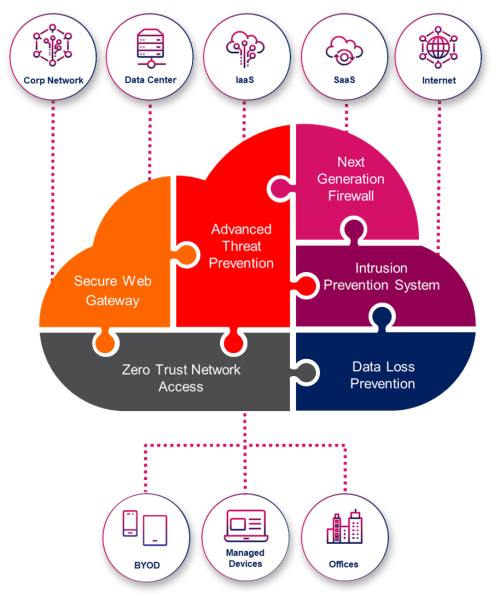
Secure Access Service Edge (SASE)
Harmony Connect is redefining SASE by making it easy to connect any user or branch to any resource, without compromising on security.
The solution unifies multiple cloud-delivered network security services and offers you the flexibility to choose between:
- Clientless and client-based remote access to enterprise applications
- Secure internet access for users and branch offices
The Industry’s Leading Network Security Is Now Available as a Cloud Service
Mobile Security
Keep your corporate data safe by securing employees’ mobile devices across all attack vectors: apps, network and OS. Perfectly fits into your existing mobile environment, deploys and scales quickly, and protects devices without impacting user experience nor privacy.


