Penetration Testing
Penetration testing is a controlled, authorized simulation of real-world attacks designed to uncover vulnerabilities before adversaries do. At Sirius, we emulate the tactics, techniques, and procedures (TTPs) of actual threat actors to expose weaknesses and demonstrate their true business impact — decisively and precisely.
Why Penetration Testing?
A penetration test goes beyond automated scans and compliance checklists. It challenges your defenses from both authenticated and unauthenticated perspectives, covering various user roles and system entry points. The result: a clear, actionable understanding of your true exposure, rather than theoretical risks.
Types of Penetration Testing
Black Box Testing
We operate with zero prior knowledge — simulating an external attacker probing your environment blindly for exploitable weaknesses.
Gray Box Testing
We start with partial knowledge (e.g., some credentials or architectural details), replicating an attacker with insider information or prior foothold.
White Box Testing
We have full access to system internals, including source code and architecture, allowing for the deepest level of assurance in the shortest time.
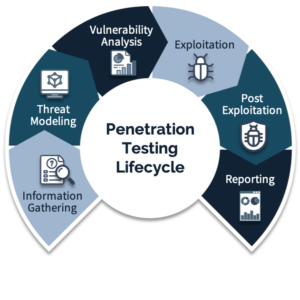
Our Approach
Reconnaissance
We collect intelligence from public and private sources — mapping your attack surface, discovering potential entry points, and profiling exposed assets.
Scanning & Enumeration
We identify vulnerabilities at the network, application, and service levels using advanced scanning tools and manual analysis.
Exploitation & Access
We simulate real-world breaches, exploiting identified vulnerabilities to gain unauthorized access, escalate privileges, and demonstrate potential business impact.
Persistence & Impact Demonstration
We illustrate how an attacker could maintain long-term access, exfiltrate or manipulate data, and disrupt operations, highlighting the full consequences of a breach.